If you would like to get LibreNMS and Oxidized working in a docker environment this will be a down and dirty way to do it. This will cover some of the helpful commands that we used for troubleshooting.
I am using CentOS 7.
** NOTE - Before you even start figure out how many devices that you will be monitoring with LibreNMS. for all the graphs and data there will be .rrd files that get created for each device..... each device's rrd files can be 90mb to 140mb. Make sure you size your OS properly before you starting so you dont have to go back and resize your disk.... it sucks.
As a reference 10k devices is around you might want to have 500GB.
Install Docker + Docker Compose
1. I went to the docker website and used the following guide to install docker.
https://docs.docker.com/engine/install/centos/
2. Once you have Docker installed go ahead and install "Docker Compose"
https://docs.docker.com/compose/install/
3. At this point you should be able to run the following command to show that you have Docker running.
systemctl status docker
Install LibreNMS with Docker Compose
1. Create directory for LibreNMS
mkdir /var/librenms/
cd /var/librenms
2. Download files
a. Go to the following site and wget all the files and place them in /var/librenms/
3. Edit the files to fit your needs.
a. I edited .env and changed "MYSQL_PASSWORD=password"
4. Run docker-compose
docker-compose up -d
5. Once it completes you should have LibreNMS install. so start it up.
systemctl start docker
6. you should have something that looks like this.... Notice there are 4 containers of LibreNMS.. dont delete any of them!!!! It will also will have created a mariadb database.
docker ps
7. If you want to check to make sure librenms is working you should be able to use curl and make sure it connects.
curl -I -v --ipv4 http://localhost:8000
8. You should be able to go to your servers IP address @ port 8000 and get the LibreNMS login screen. librenms/librenms for the user/pass.
Install Oxidized with Docker-Compose
1. Create oxidized directory
mkdir /var/oxidized/
2. Get files oxidized with docker-compose
nano docker-compose.yml
# docker-compose.yml
# docker-compose file example for oxidized that will start along with docker daemon
oxidized:
restart: always
image: oxidized/oxidized:latest
ports:
- 8888:8888/tcp
environment:
CONFIG_RELOAD_INTERVAL: 600
volumes:
- /etc/oxidized:/root/.config/oxidized
3. Run docker-compose
docker-compose up -d
4. You might have to allow port 8888 through your firewall. You can check this by:
semanage port -l | grep http_port_t
a. If port 8888 is not there use the following to add it.
sudo semanage port -a -t http_port_t -p tcp 8888
b. Restart firewall
systemctl stop firewalld
systemctl start firewalld
5. You should have Oxidized installed now. Stop/Start docker and show the status.
systemctl stop docker
systemctl start docker
systemctl status docker
Working with in the Docker Containers
1. At this point you should have both LibreNMS and Oxidized both running. To get into the Oxidized container is pretty easy as it is the only one. Use the following command.... keep in mind the "bc2" will be different for your Container ID.
docker exec -it bc2 /bin/bash
. If you need to edit the Oxidized config file it will be located at: nano /root/.config/oxidized/config
2. The LibreNMS containers are a little tricky as there are 4 of them that look the same.
You will need to find the one that just says "librenms" to actually change the config file. I am snipping 2 pictures together because the text is to long.
3. Get into the LibreNMS container using the following.... replace the "235" with your Container ID.
docker exec -it 235 /bin/bash
a. To edit the LibreNMS config go to the following once you are in the container.
vi /opt/librenms/config.php
b. If you would like to scan a network to look for devices use the following command while you are in the LibreNMS container
python3 snmp-scan.py -r X.X.X.X/X
Tips
- Once you get everything going take a snapshot of your VM.
- The formatting is VERY important within Oxidized and LibreNMS... If you reload docker after a change and your container will not start or HTTP will not load go back and check the formatting.
- If oxidized is erroring out because it can not find your switch/firewall model you might have to add it. Add it at the following location within your Oxidized container.
- cd /var/lib/gems/2.5.0/gems/oxidized-0.28.0/lib/oxidized/model
- Deleting a device - need to be in the LibreNMS container
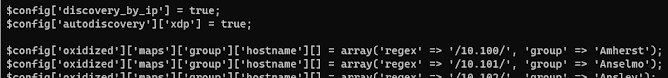
- If you have multiple locations that you manage and you want to organize them within Oxidized so LibreNMS can see them in a more useable way you can change the group so that they will be placed in the correct group. Below is an example of how we have don that based on the first 2 octets of the ip address.
- This is in the LibreNMS container under /opt/librenms.config.php
- If you are having trouble with a device not pulling the correct group use the following to see all of the variables that it is pulling.
- curl -H 'X-Auth-Token: token-created-in-Libre-GUI' http://X.X.X.X:8000/api/v0/devices/X.X.X.X
- The LibreNMS containers are built on Alpine Linux. If you want to install a package use...